For more than a decade, the DevSecOps movement has pushed a singular message: embed security into every stage of the software development lifecycle. But while we’ve automated scanners, built smarter CI/CD pipelines, and integrated SAST into version control, one piece has remained stubbornly manual—people.
Security champions have long been hailed as the missing link: developers embedded within teams who understand code and care about security. They’re the bridge between AppSec and engineering. But as any CISO or AppSec manager will tell you, building a security champions program is hard. Keeping it alive is even harder.
That’s why Arnica’s newly launched “Security Champions with Arnica” feature deserves serious attention. It doesn’t just add another tool to the security stack. It automates a human process we’ve been fumbling for years—and in doing so, it could fundamentally change how we scale secure software practices.
Talk to any enterprise with more than 50 engineers and you’ll hear the same story. “We tried to build a champions program. We asked for volunteers. A few stepped up. Some lost interest. Eventually it fizzled.”
Why does this happen? Because the traditional model relies too heavily on social engineering. Managers nominate developers. AppSec teams create slide decks. There’s a kickoff meeting, maybe a Slack channel, and then… inertia.
Even in successful programs, measuring impact is a guessing game. Are champions actually resolving more vulnerabilities? Are they mentoring peers? Or just carrying the title? The gap between visibility and accountability remains wide.
A 2024 Nominet survey revealed a staggering insight: organizations with an active champions program were 65% less likely to experience a data breach. Yet most companies struggle to make that program function in practice. The problem isn’t the idea of champions—it’s the lack of infrastructure to support it at scale.
Arnica’s Automation Changes the Rules
What makes “Security Champions with Arnica” different is that it bypasses the nomination process altogether. Instead of asking, “Who wants to be a security champion?” Arnica asks: Who’s already behaving like one?
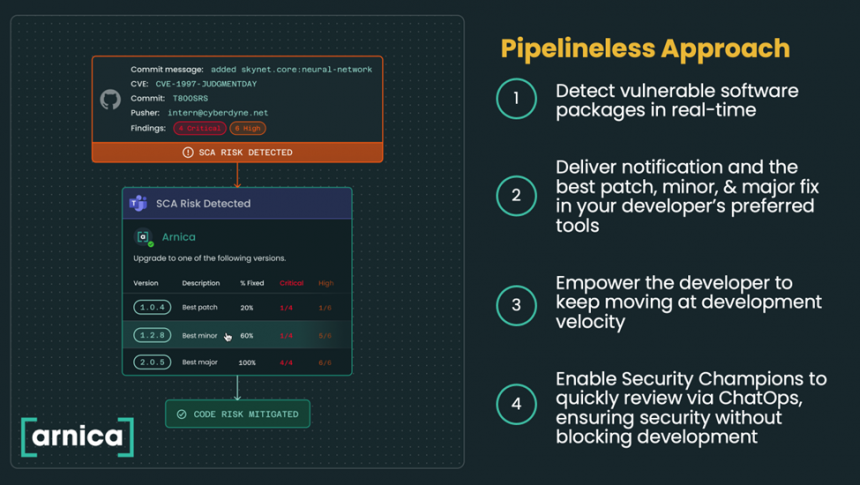
Using behavioral analysis, Arnica monitors real developer activity—who’s fixing vulnerabilities, who’s flagging security issues in code reviews, who’s consistently committing secure code. These signals are quietly, continuously collected and analyzed. The system identifies developers demonstrating secure behavior, and surfaces them as candidates for champion roles.
No sign-up. No guesswork. Just data.
This shift—from manual designation to behavior-based discovery—is significant. It turns a subjective HR process into an objective, repeatable practice. And once identified, these champions aren’t given busywork or asked to attend another meeting. They’re engaged through the tools they already use—GitHub, Slack, Microsoft Teams, Azure DevOps—and given real-time opportunities to act on security issues in the flow of development.
Why This Matters for DevSecOps at Scale
The value here is more than philosophical. It’s operational.
The harsh truth is that most AppSec teams are outnumbered. A single security engineer might be responsible for 100 developers or more. Scaling that support model requires distributing ownership of security without turning every dev into a full-time security expert.
By identifying those who are already security-conscious—and automating the way they’re looped into key moments—Arnica creates a lightweight security mesh inside engineering teams. Each champion handles issues relevant to their codebase, makes informed decisions (with guardrails), and only escalates to central AppSec when needed.
This structure solves two major problems:
- Speed: Vulnerabilities are addressed in real time, often in pull requests, without waiting for AppSec triage.
- Focus: Developers aren’t overwhelmed with alerts. The system knows who owns what and routes issues accordingly.
It’s no longer about shifting left. It’s about embedding responsibility right where the code lives—and doing so without ceremony.
Not Just Another Dashboard
Perhaps most impressively, Arnica does this without forcing developers into another UI.
Everything happens in the tools developers are already using. A risky commit? Arnica flags it in the PR. A dismissed vulnerability? The champion gets pinged in Slack for approval. Need to audit who fixed a CVE across 12 repos? The system tracks it natively, complete with context-rich Jira tickets.
Access control is also deeply considered. Developers only see vulnerabilities relevant to their work. Champions get scoped views across their assigned products. And admins can enforce row-level and product-level security policies to avoid unnecessary data exposure.
This granular permission model ensures that scaling doesn’t come at the expense of compliance or developer trust. Everyone sees what they need—and only what they need.
From Risk Reduction to Career Advancement
There’s also a subtle but powerful benefit: career development.
In most companies, security work by developers goes unnoticed. Fix a critical bug? You might get a thumbs-up. Actively prevent a vulnerability? No one even sees it.
With Arnica, that changes. The system tracks which developers are closing security tickets, mitigating risks early, and proactively reviewing code. That visibility translates to influence. Developers who act as champions build a track record that engineering leadership—and eventually HR—can see.
In a tight hiring market where internal growth matters, this visibility helps security-conscious developers advance. It gives AppSec a new value proposition: participate in security, and we’ll help you build your career.
The Bottom Line
What makes Arnica’s “Security Champions” feature remarkable isn’t just its technical elegance. It’s that it operationalizes a concept the industry has long agreed on but failed to execute at scale.
By blending behavioral analytics, pipelineless scanning, native workflow integrations, and granular access control, Arnica has created what might be the first truly scalable security champions platform.
For security leaders, this changes the calculus. It means you no longer need to convince 500 developers to “care more about security.” Instead, you let your top 20% lead by example—and give them the tooling to make a real difference.
And in a world where the speed of development shows no sign of slowing, that might be the inflection point DevSecOps has been waiting for.